
Getty Images
Malware recently spotted in the wild uses sophisticated measures to disable antivirus protections, destroy evidence of infection, and permanently infect machines with cryptocurrency-mining software, researchers said Tuesday.
Key to making the unusually complex system of malware operate is a function in the main payload, named GhostEngine, that disables Microsoft Defender or any other antivirus or endpoint-protection software that may be running on the targeted computer. It also hides any evidence of compromise. “The first objective of the GhostEngine malware is to incapacitate endpoint security solutions and disable specific Windows event logs, such as Security and System logs, which record process creation and service registration,” said researchers from Elastic Security Labs, who discovered the attacks.
When it first executes, GhostEngine scans machines for any EDR, or endpoint protection and response, software that may be running. If it finds any, it loads drivers known to contain vulnerabilities that allow attackers to gain access to the kernel, the core of all operating systems that’s heavily restricted to prevent tampering. One of the vulnerable drivers is an anti-rootkit file from Avast named aswArPots.sys. GhostEngine uses it to terminate the EDR security agent. A malicious file named smartscreen.exe then uses a driver from IObit named iobitunlockers.sys to delete the security agent binary.
“Once the vulnerable drivers are loaded, detection opportunities decrease significantly, and organizations must find compromised endpoints that stop transmitting logs to their SIEM,” the researchers wrote, using the abbreviation for security information and event management. Their research overlaps with recent findings from Antiy.
Once the EDR has been terminated, smartscreen.exe goes on to download and install XMRig, a legitimate application for mining the monero cryptocurrency that’s often abused by threat actors. A configuration file included causes all coins created to be deposited into an attacker-controlled wallet.
The infection chain starts with the execution of a malicious binary that masquerades as the legitimate Windows file TiWorker.exe. That file runs a PowerShell script that retrieves an obfuscated script, titled get.png, which downloads additional tools, modules, and configurations from an attacker-controlled server. Elastic Security Labs provided the following graphic that illustrates the entire execution flow:
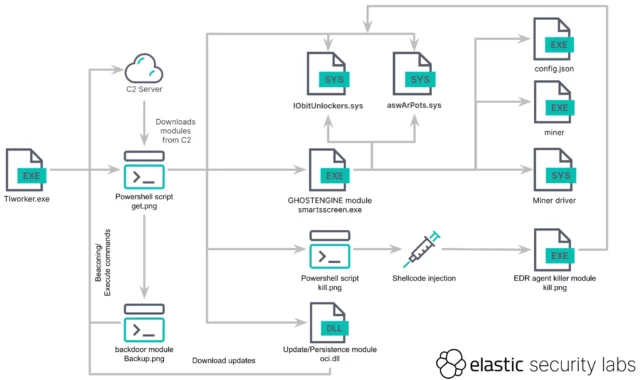
Elastic Security Labs
GhostEngine also runs several files that allow the malware to gain persistence, meaning it loads each time the infected machine restarts. To do this, the file responsible, name get.png, creates the following scheduled tasks with SYSTEM, the highest system privileges in Windows:
- OneDriveCloudSync using msdtc to run the malicious service DLL C:\Windows\System32\oci.dll every 20 minutes (described later)
- DefaultBrowserUpdate to run C:\Users\Public\run.bat, which downloads the get.png script and executes it every 60 minutes
- OneDriveCloudBackup to execute C:\Windows\Fonts\smartsscreen.exe every 40 minutes
A separate component can act as a backdoor that allows the attackers to further download and execute malware on the infected machine. A PowerShell script titled backup.png “functions like a backdoor, enabling remote command execution on the system,” the researchers wrote. “It continually sends a Base64-encoded JSON object containing a unique ID, derived from the current time and the computer name while awaiting base64-encoded commands. The results of those commands are then sent back.”
The researchers extracted the file the malware used to configure XMRig. It established a payment ID of:
468ED2Qcchk4shLbD8bhbC3qz2GFXqjAUWPY3VGbmSM2jfJw8JpSDDXP5xpkMAHG98FHLmgvSM6ZfUqa9gvArUWP59tEd3f
The ID allowed the researchers to view the worker and pool statistics on one of the Monero Mining Pool sites listed in the configuration.
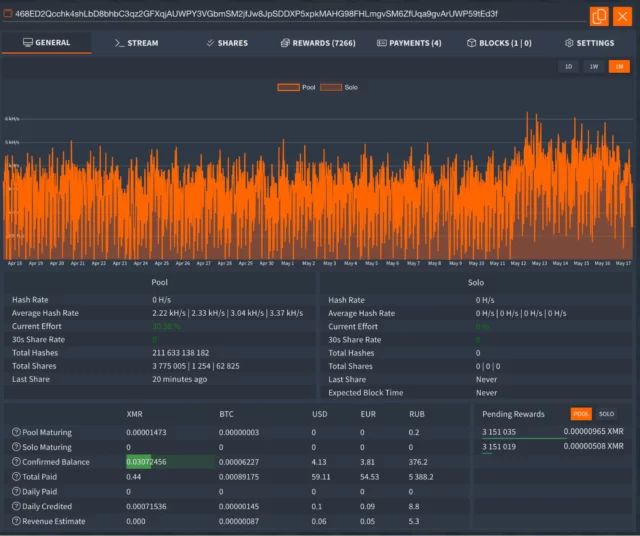
Elastic Security Labs
The payment ID showed XMRig had netted the attackers only a little more than $60. The researchers, however, noted that other machines infected in the same campaign would be given different IDs that may have generated larger amounts of monero.
Because the campaign successfully disables an array of EDR protections, administrators must rely on other means to discover infections inside their networks. The researchers have released a set of YARA rules that will flag infections. They work primarily by detecting the presence of the GhostEngine malware and the installation of the Avast and IOBit drivers. Tuesday’s post also provides a list of file hashes, IP addresses, and domain names that will indicate targeting or infection.

















+ There are no comments
Add yours