
Getty Images
Mac malware that steals passwords, cryptocurrency wallets, and other sensitive data has been spotted circulating through Google ads, making it at least the second time in as many months the widely used ad platform has been abused to infect web surfers.
The latest ads, found by security firm Malwarebytes on Monday, promote Mac versions of Arc, an unconventional browser that became generally available for the macOS platform last July. The listing promises users a “calmer, more personal” experience that includes less clutter and distractions, a marketing message that mimics the one communicated by The Browser Company, the start-up maker of Arc.
When verified isn’t verified
According to Malwarebytes, clicking on the ads redirected Web surfers to arc-download[.]com, a completely fake Arc browser page that looks nearly identical to the real one.
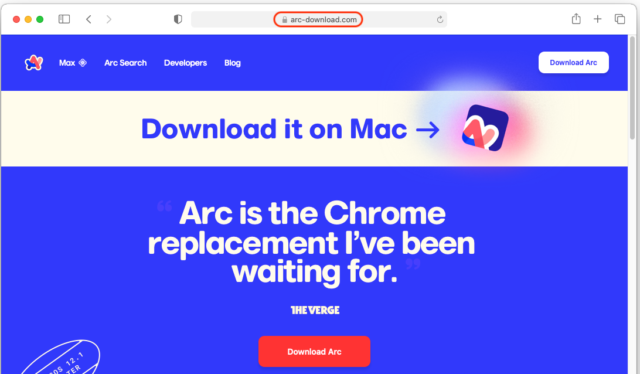
Malwarebytes
Digging further into the ad shows that it was purchased by an entity called Coles & Co, an advertiser identity Google claims to have verified.
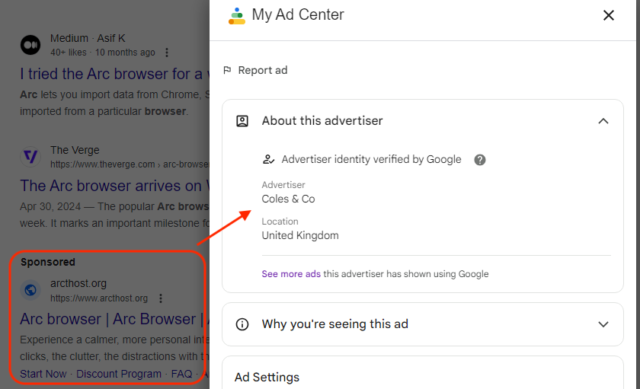
Malwarebytes
Visitors who click the download button on arc-download[.]com will download a .dmg installation file that looks similar to the genuine one, with one exception: instructions to run the file by right-clicking and choosing open, rather than the more straightforward method of simply double clicking on the file. The reason for this is to bypass a macOS security mechanism that prevents apps from being installed unless they’re digitally signed by a developer Apple has vetted.
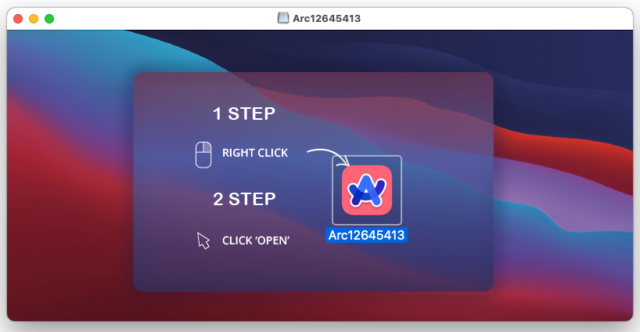
Malwarebytes
An analysis of the malware code shows that once installed, the stealer sends data to the IP address 79.137.192[.]4. The address happens to host the control panel for Poseidon, the name of a stealer actively sold in criminal markets. The panel allows customers to access accounts where data collected can be accessed.

Malwarebytes
“There is an active scene for Mac malware development focused on stealers,” Jérôme Segura, lead malware intelligence analyst at Malwarebytes, wrote. “As we can see in this post, there are many contributing factors to such a criminal enterprise. The vendor needs to convince potential customers that their product is feature-rich and has low detection from antivirus software.”
Poseidon advertises itself as a full-service macOS stealer with capabilities including “file grabber, cryptocurrency wallet extractor, password stealer from managers such as Bitwarden, KeePassXC, and browser data collector.” Crime forum posts published by the stealer creator bill it as a competitor to Atomic Stealer, a similar stealer for macOS. Segura said both apps share much of the same underlying source code.
The post author, Rodrigo4, has added a new feature for looting VPN configurations, but it’s not currently functional, likely because it’s still in development. The forum post appeared on Sunday, and Malwarebytes found the malicious ads one day later. The discovery comes a month after Malwarebytes identified a separate batch of Google ads pushing a fake version of Arc for Windows. The installer in that campaign installed a suspected infostealer for that platform.
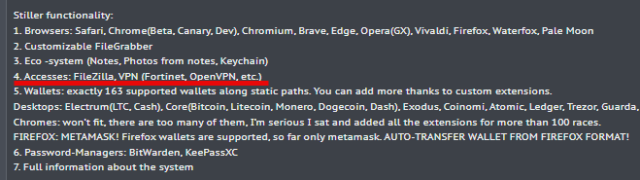
Malwarebytes
Like most other large advertising networks, Google Ads regularly serves malicious content that isn’t taken down until third parties have notified the company. Google Ads takes no responsibility for any damage that may result from the oversights. The company said in an email it removes malicious ads once it learns of them and suspends the advertiser and has done so in this case.
People who want to install software advertised online should seek out the official download site rather than relying on the site linked in the ad. They should also be wary of any instructions that direct Mac users to install apps through the double-click method mentioned earlier. The Malwarebytes post provides indicators of compromise people can use to determine if they’ve been targeted.


















+ There are no comments
Add yours